Pentester Academy Certified Enterprise Security Specialist (PACES) is the certification challenge for anyone who’s completed the course GCB Cyber Range. https://www.pentesteracademy.com/gcb
This course is ideal for those who are familiar with the penetration testing methodology and reasonably comfortable with AD enumeration. Like any other penetration testing courses out there, GCB enforces the “Enumeration, Enumeration and Enumeration” motto if you want to progress from your initial box (Sutdent Machine) to Enterprise ownage. The infrastructure is HUGE and covers a variety of scenarios and each comes with a unique set of challenges. There are multiple forests in the infrastructure and each of these have a unique misconfiguration that you have find and exploit to get access. The diagram below is somewhat accurate.
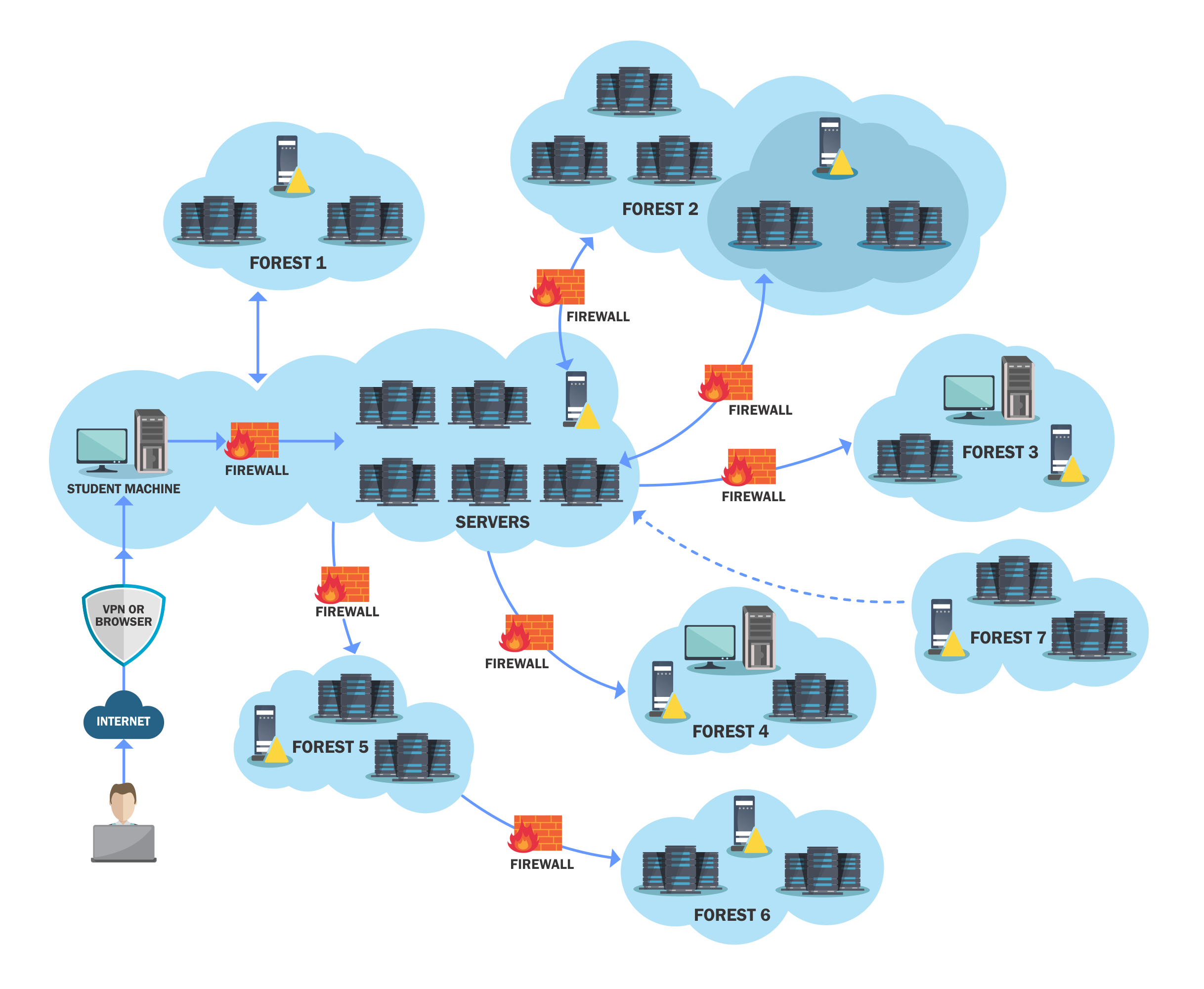
As mentioned on their website, indeed this course is not for the faint hearted. 450 hours of torture is an understatement! It is definitely tough and requires a lot of research on your part to progress through the lab.

This course does not provide a guide or a walkthrough for the challenge but you get hints in the form of network diagrams which provides a pathway through the challenge. However, the GCB team (massive shoutout to them) is wonderful and you can always reach out to them if you get stuck.
Course Details
The GCB Cyber Range infrastructure is a fully patched Windows AD environment. You are expected to exploit AD misconfigurations and weaknesses for lateral movement and progressing through the challenge.

In GCB, you will learn how to exploit misconfigurations and abuse LAPS, JEA, WSL, RCBD, WSUS and other Windows services to “capture the flag”. The flag is a file containing a code that is locked away in a completely air gapped environment which will be available to you once you’ve compromised all the forests in the infrastructure.
Exam
The exam is similar to its predecessors (Windows Red Team Lab). The exam is a fully patched Windows Server 2019 environment but there’s a twist. This time, you are expected to secure the AD environment that you’ve compromised. The exam pays equal weightage to Attack and Defense aspect.
Recommendations
- Enumerate, Enumerate, Enumerate. More enumeration will help you in figuring out a pathway to other forests.
- Bloodhound is amazing but do not rely fully on Bloodhound to show you the path. Be comfortable with manual AD enumeration and how it works.
- If you get stuck, try to spend some time exhausting all your searches before you reach out to the support team. You will learn a lot in that process.
- The environment simulates a real environment with real people in there. Thinking like them will help you find places where you can find interesting things.
- Post-Exploitation enumeration is the key to success! Do not rely solely on creds from lsass for lateral movement.
- Notes keeping is the key! Having a checklist of pre and post exploitation activities and a central loot for credentials would help you a lot.
- Try as many tools/techniques as possible. Having multiple scripts/tools/techniques for the same task will help improve your testing methodology.
- Do not forget to use your penetration testing methodology when AD enumeration does not present a path.
Final Thoughts
Overall, this is one of the hardest and most rewarding certifications that I have done so far. Nikhil Mittal’s hard work and expertise definitely shows in this course. Amazing work done by him and the team to present such a good learning experience and thanks to Pentester Academy for providing the platform.