TL;DR – MAPI can be abused to go through a user’s mailbox for sensitive information.
Messaging Application Programming Interface (MAPI) is an API that allows programs/applications to interface with Outlook and become email-aware. Using MAPI, a program can interact with outlook application to perform actions such as send/receive emails.
This could be immensely helpful in scenarios where you’ve managed to get your initial foothold through phishing and you want to go through their emails for specific keywords such as passwords, information on trade secrets or finances, network information etc. without knowing their password or accessing their inbox through OWA.
Here’s a proof-of concept (PoC) written in python. https://github.com/virenium/outmapify
Implementation in C# is also possible which may require the Interop Outlook dll as reference in the assembly.
This PoC relies heavily on pypiwin32 (https://pypi.org/project/pypiwin32/ ) package and credits to the maintainers for their work. To run this as a standalone application, PyInstaller (https://www.pyinstaller.org/) would be required to compile an executable for Microsoft Windows.
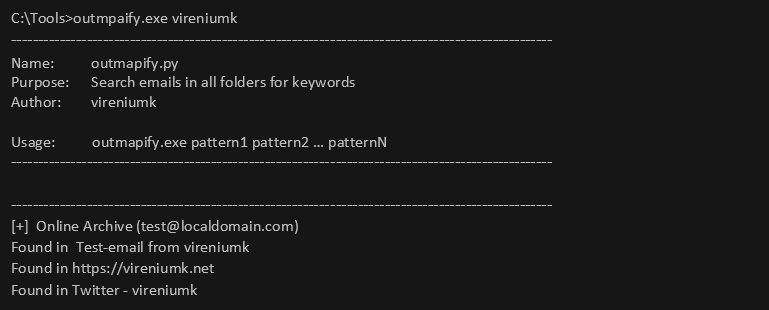
This script will go through all the mailboxes a user can access and print the Subject of the email and write the body of the email in a file called output.txt in your current folder.
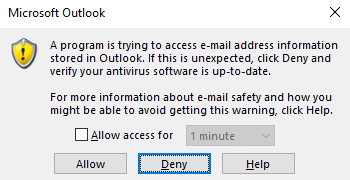
Based on the outlook configuration, this may pop up on the victim side. This can be suppressed by modifying certain registry values. I will leave this to your creativity.